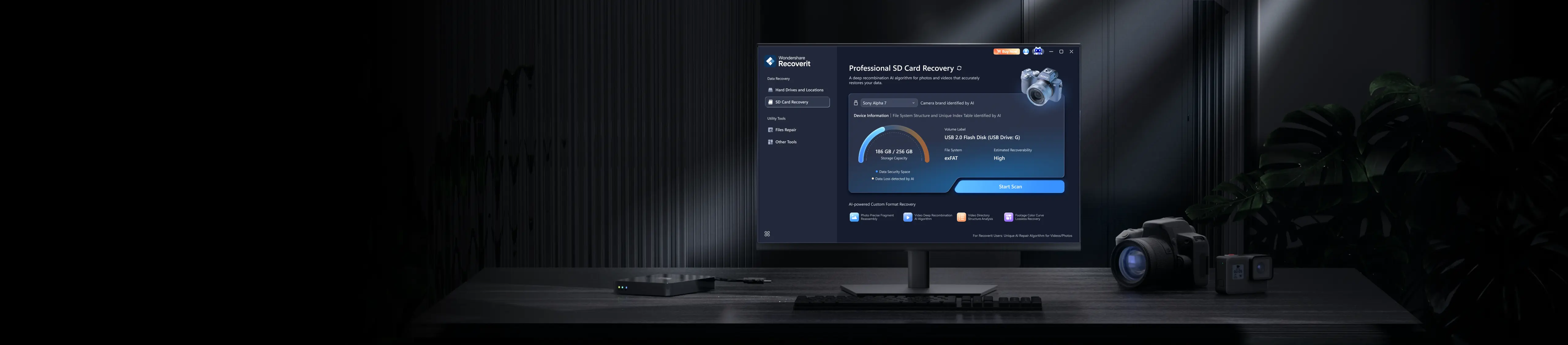
Recover Data Like Videos, Photos, And Other Files With AI
AI-Powerd SD Card & External Devices Recovery
Recover lost or deleted files from SD cards, USB drives, and external devices.

AI data recovery support all brand SD card data recovery and external disk drive data recovery. major devices data recovery is supported.

AI identification for over a million devices, including digital cameras, drones, GoPro, handheld devices, disks, Mac devices, and more.

Intelligently diagnose user file loss scenarios based on device information and deliver professional, customized recovery solutions.
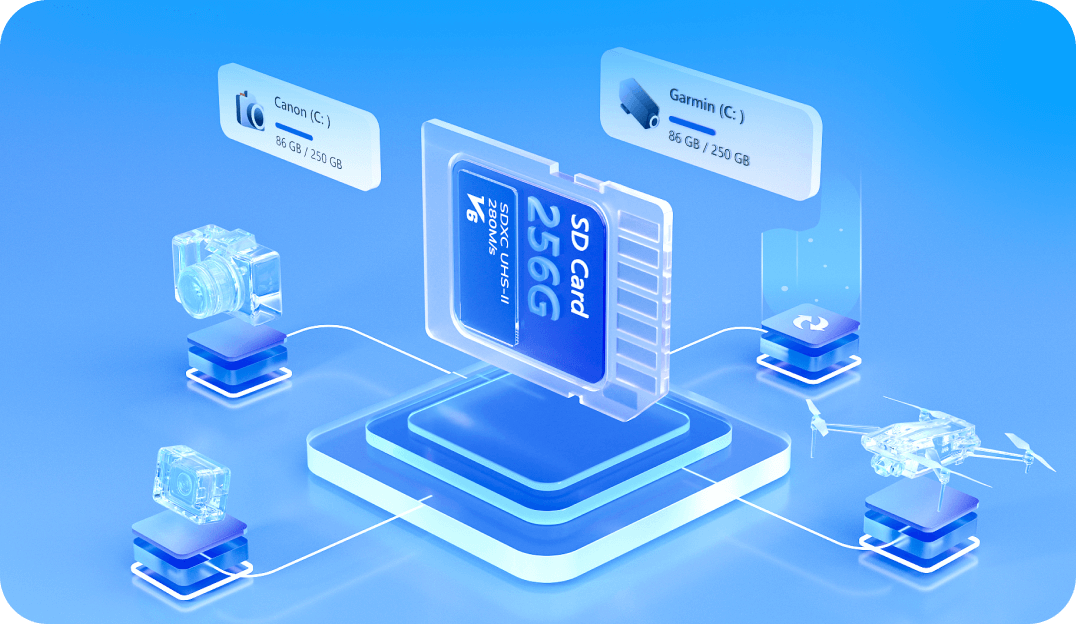
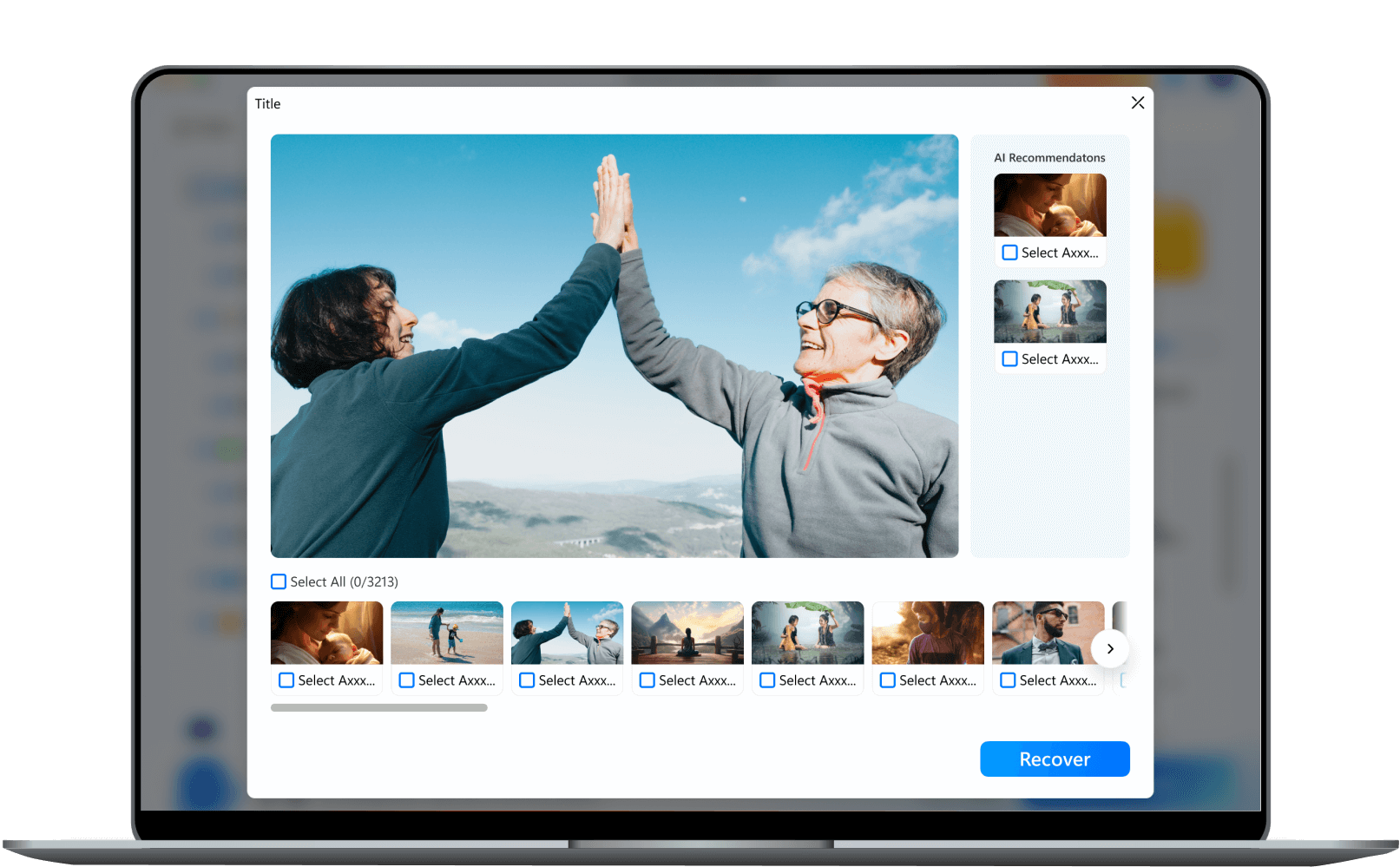
AI Enhanced Photo & Video Recovery
Recover your lost, deleted, or deeply hidden videos and photos, and retrieve all files from all devices.

AI data recovery for all kinds of video and photo files, including home surveillance videos and driving recorder videos. Whether lost, deleted, or deeply hidden.

Industry-leading JPEG fragment reassembly recover solution, apply deep scan technology to video defragmentation (patented). The recovery rate of accidentally deleted photos up to 80%.

AI Enhance old, blurry, or low-clarity photos and videos after recover, supporting a final output resolution of up to 8K.
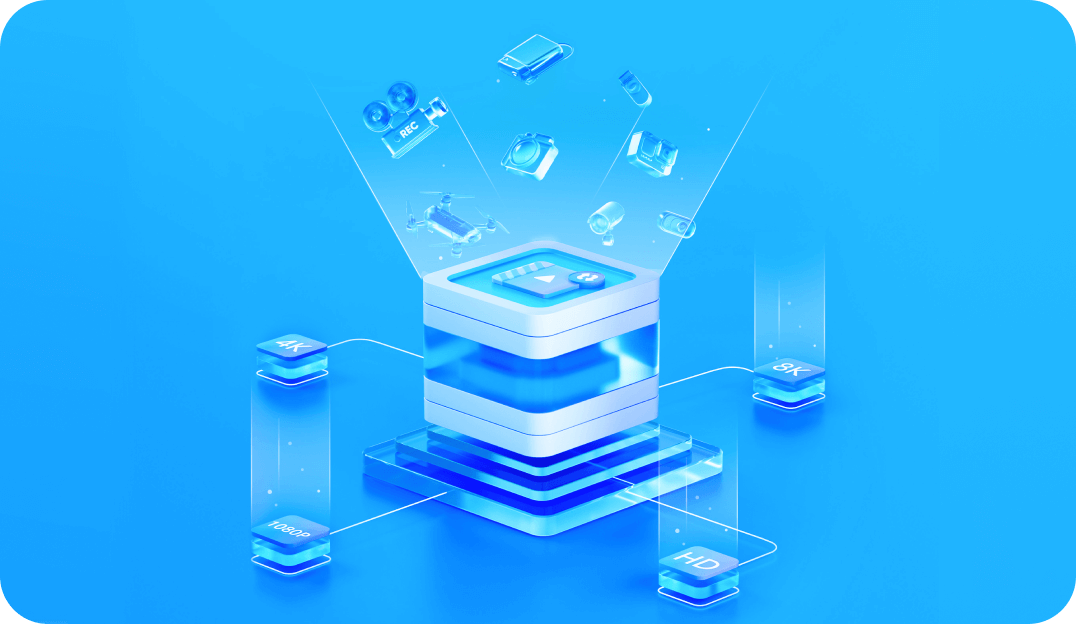
Advanced Corrupted File Repair
Repair corrupted file in any scenario and enhance photos with AI

AI Recording after a crash, water damage, shaking, falling, battery dead, unexpected shutdown during video recording, etc.

AI photo repair Sharpen blurred image details, clarify low-quality images, refine facial features, and enhance overall image quality.

The lost video was recovered but failed to play for some unknown reasons.
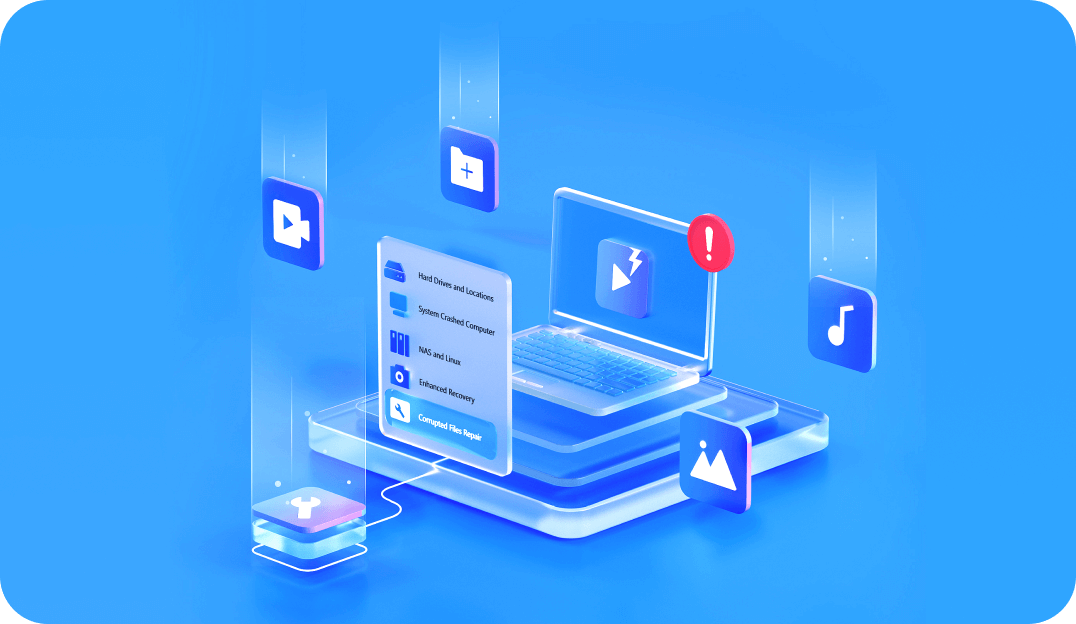
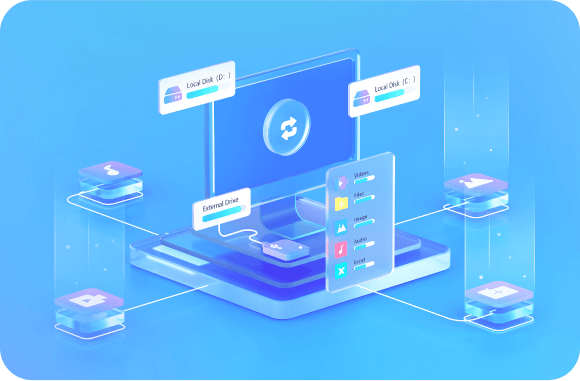

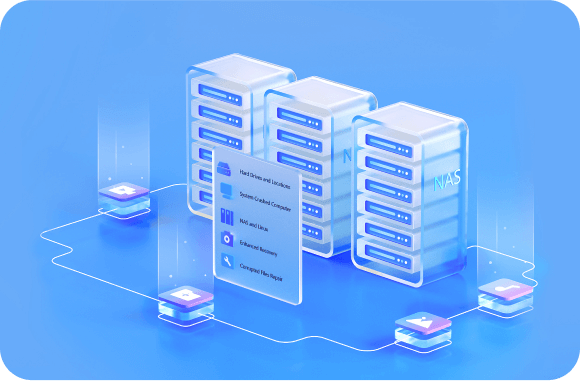

Explore More Features Of Recoverit Data Recovery Expert

Recoverit not only recovers data emptied from the recycle bin but also retrieves permanently deleted files—even from physical hard drive damage, recycle bin overflow, or system cleanups.

A disk image is a mirrored copy of a storage device. Recoverit works well as a disk image software that allows you to recover files from previously created disk images.

BitLocker is a Windows security and encryption feature. Recover BitLocker data recovery software helps you recover deleted data from BitLocker encrypted drives.

Recovery software can scan for lost partitions and recover files from damaged ones, bringing professional data recovery capabilities to everyday Windows users.
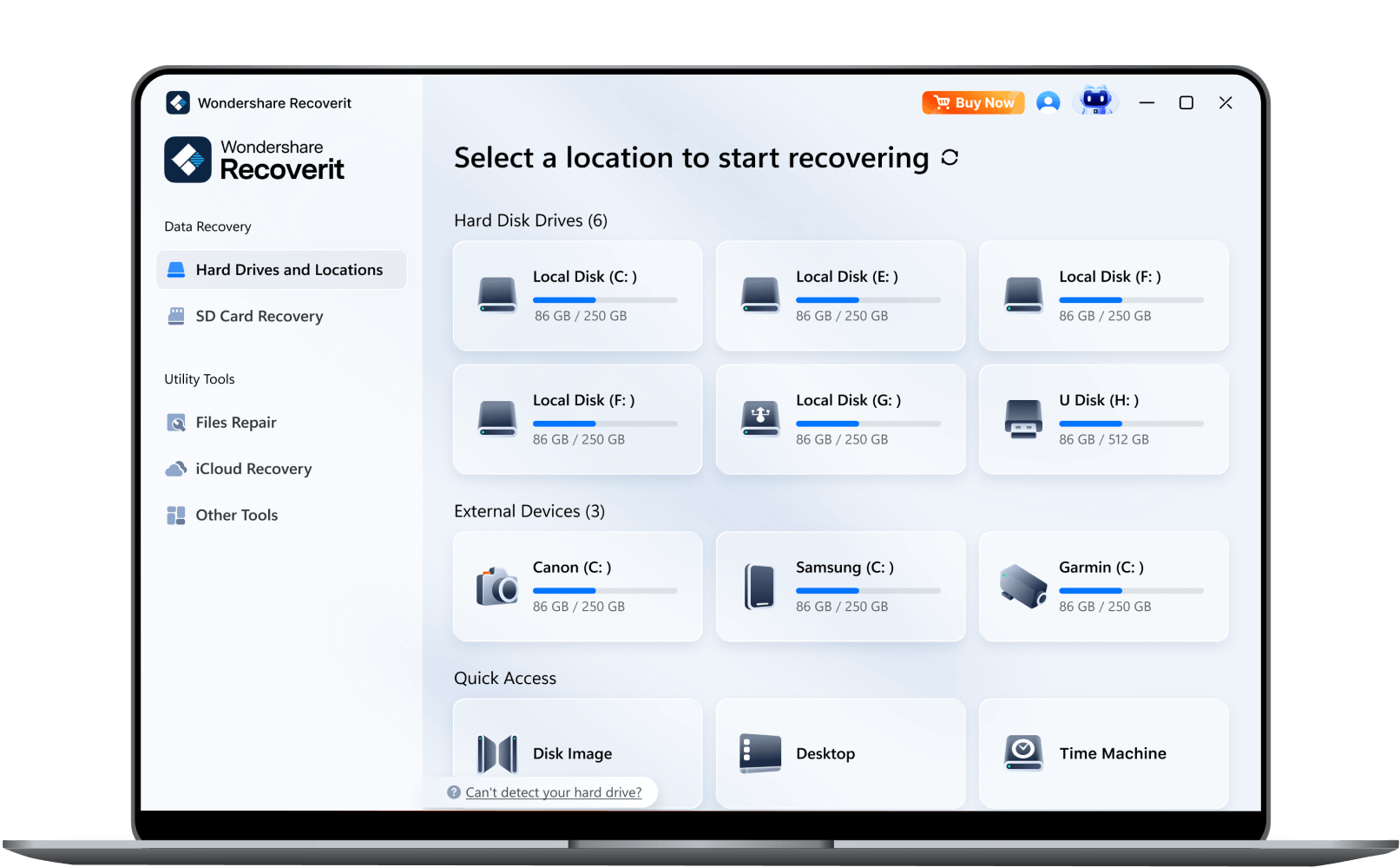
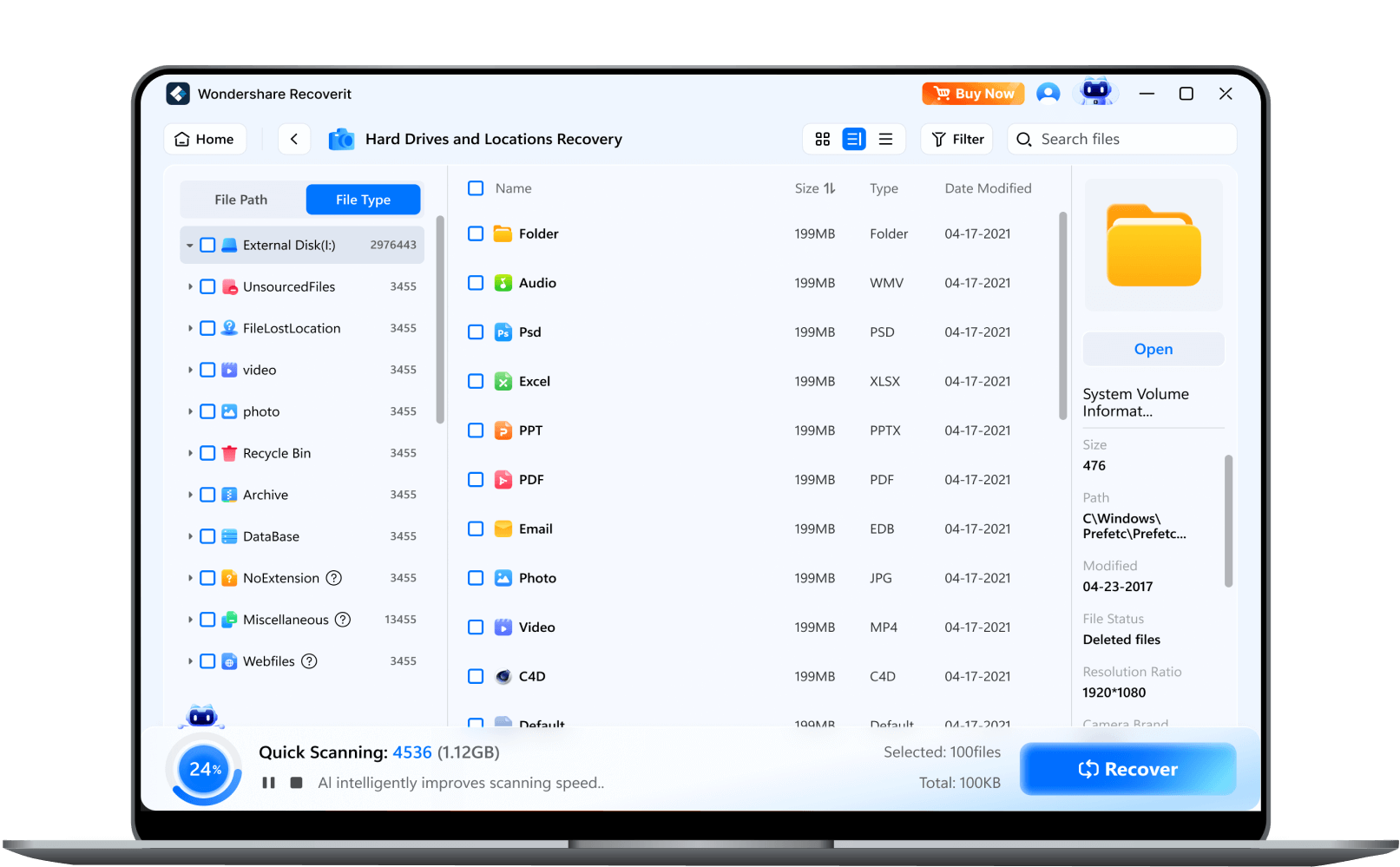
3 Steps To Retrieve Data With Recoverit
Recoverit is dedicated to more straightforward, secure, and intuitive technology for data recovery. Thus, you can bring back all your videos and files in 3 steps.
Trusted By Over 100 Million Users & Leading Brands


It is possible to recover deleted files from Mac using Recoverit. It brings a redesigned user interface that simplifies the process to recover deleted data from Mac - so now you only need to scan your system once to find your files. Scanning is much faster and preview boxes are bigger.


Wondershare Recoverit Data Recovery is the most popular software and trusted by customers on Interesting Engineering. You can download Recoverit Data Recovery software for free.


Recoverit promises to help you recover lost data with a high recovery rate, making the process as easy as possible. Both available for Windows and macOS, Recoverit is here to recover all file types including photos, videos, and documents.


It is possible to recover deleted files from Mac using Recoverit. It brings a redesigned user interface that simplifies the process to recover deleted data from Mac - so now you only need to scan your system once to find your files. Scanning is much faster and preview boxes are bigger.


Wondershare Recoverit Data Recovery is the most popular software and trusted by customers on intelligent. You can download Recoverit Data Recovery software for free.


Recoverit promises to help you recover lost data with a high recovery rate, making the process as easy as possible. Both available for Windows and macOS, Recoverit is here to recover all file types including photos, videos, and documents.

"Two weeks ago, I accidentally formatted my hard drive, wiping out 500GB of work files and precious photos. I tried Recoverit, a data recovery tool with deep scan capabilities. It was easy to use and recovered 95% of my files, including high-res images and raw footage. Recoverit saved me from a huge loss and taught me the importance of regular backups and reliable recovery tools."

"I accidentally reformatted my SD card after a family gathering and lost all my photos and videos. After trying several recovery tools, only my photos were recovered; the videos remained corrupted. Since I use Wondershare for compression, I gave Recoverit a try. The scan felt endless, but in the end, Recoverit successfully recovered all my videos. I'm so grateful—wish I had tried it sooner!"

"I'm a math student relying on online platforms for coursework. One evening, my files—assignments, notes, and solved problems—were deleted due to a sync error. Panic set in as midterms loomed. I tried Recoverit, hoping for a miracle. After a tense scan, it recovered every lost file. I was relieved and grateful—my hard work was saved, and I learned the value of reliable backup and recovery tools."

"I made a huge mistake at work—I added multiple sheets to a CSV file, thinking it worked like an XLSX file. When I saved, one crucial sheet disappeared. After learning CSVs can only hold one sheet and my sheet seemed lost forever, I tried Recoverit. To my relief, it recovered my lost data, not perfectly formatted but intact. Recoverit saved my project and my peace of mind."

"I used a 360 camera on a group jump, but the video file got corrupted and wouldn't open. After trying Reddit tips and copying the file to my computer, it still didn't work. Then I tried Recoverit. Its deep scan took about an hour, but it pieced the video together frame by frame. I thought the footage was lost forever, but Recoverit brought it back—I can now edit the full story of my skydive."

"Two weeks ago, I accidentally formatted my hard drive, wiping out 500GB of work files and precious photos. I tried Recoverit, a data recovery tool with deep scan capabilities. It was easy to use and recovered 95% of my files, including high-res images and raw footage. Recoverit saved me from a huge loss and taught me the importance of regular backups and reliable recovery tools."

"I accidentally reformatted my SD card after a family gathering and lost all my photos and videos. After trying several recovery tools, only my photos were recovered; the videos remained corrupted. Since I use Wondershare for compression, I gave Recoverit a try. The scan felt endless, but in the end, Recoverit successfully recovered all my videos. I'm so grateful—wish I had tried it sooner!"

"I'm a math student relying on online platforms for coursework. One evening, my files—assignments, notes, and solved problems—were deleted due to a sync error. Panic set in as midterms loomed. I tried Recoverit, hoping for a miracle. After a tense scan, it recovered every lost file. I was relieved and grateful—my hard work was saved, and I learned the value of reliable backup and recovery tools."

"I made a huge mistake at work—I added multiple sheets to a CSV file, thinking it worked like an XLSX file. When I saved, one crucial sheet disappeared. After learning CSVs can only hold one sheet and my sheet seemed lost forever, I tried Recoverit. To my relief, it recovered my lost data, not perfectly formatted but intact. Recoverit saved my project and my peace of mind."

"I used a 360 camera on a group jump, but the video file got corrupted and wouldn't open. After trying Reddit tips and copying the file to my computer, it still didn't work. Then I tried Recoverit. Its deep scan took about an hour, but it pieced the video together frame by frame. I thought the footage was lost forever, but Recoverit brought it back—I can now edit the full story of my skydive."

Since 2003

been helping

Guarantee

Guarantee

Support