Secure
Securely wipe your phone with Military Specifications. Protect your privacy with comprehensive data sanitization.

Fast
Increase your device erasure efficiency with high-speed data erasure and device diagnostics.

Comprehensive
The comprehensive data erasure reports and device diagnostics help add trust and value when you resell the device.

Erase All Kinds of Personal Data
Wipe Every Bit of Data Beyond Recovery
Verifiable Data Erasure Reports Brings Trust

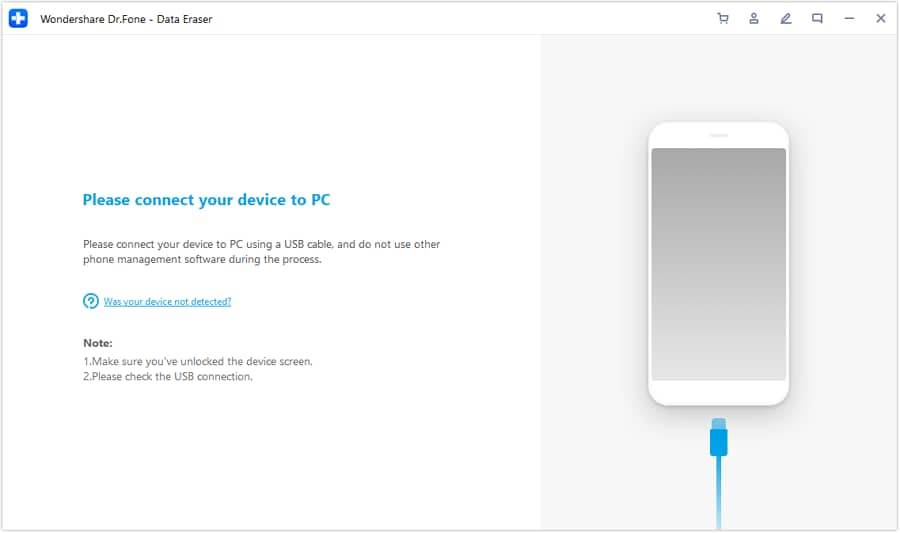
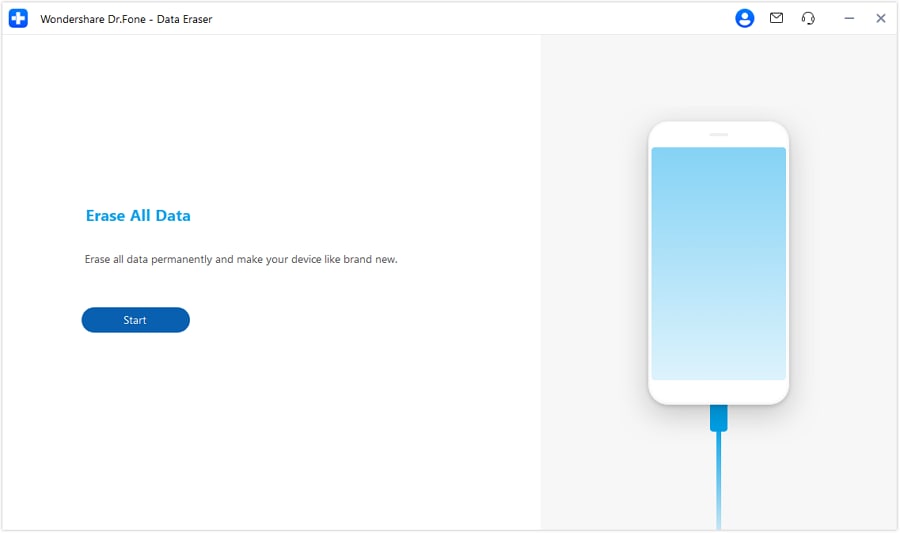
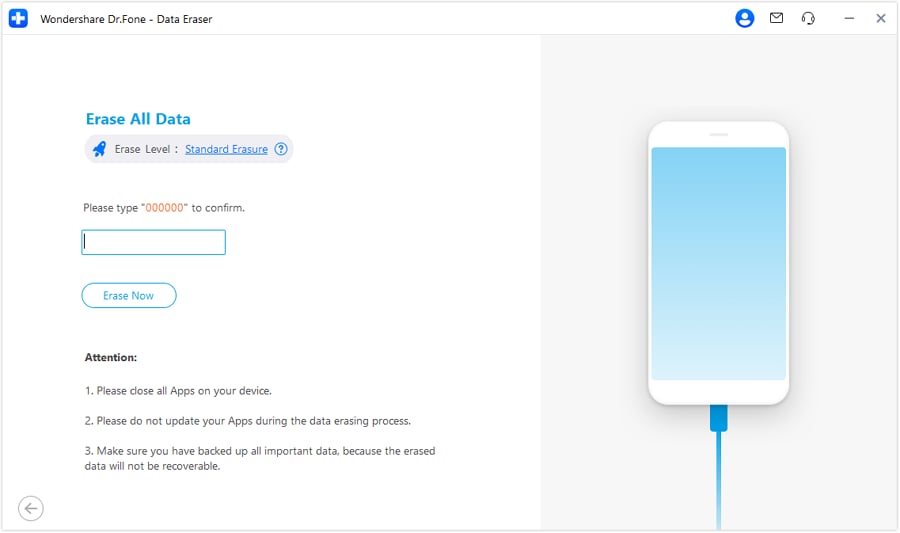
Steps for Using Data Eraser
Tech Specs
Processor
RAM
Hard Disk Space
Android OS
Computer OS
Requires macOS X 10.8 & higher
Android Data Eraser FAQs
-
Does Dr.Fone - Data Eraser (Android) completely erase all data on the phone?Yes, this Android data eraser completely and permanently wipes all the personal data on the phone, including contacts, messages, photos, call logs, calendars, app and app data, etc.
-
What should I pay attention to when I use Dr.Fone - Data Eraser (Android)?Traditional factory data reset does not erase your personal data on the phone 100%. Android Data Eraser helps you wipe the Android device clean and get it back to factory settings. Please do not disconnect the phone or open any other Android management software during the whole process. At the end, follow the instructions on Android Data Eraser to perform a factory reset on your phone.
-
What Android devices does the Android Data Eraser support?Currently, this Android data eraser supports all Android devices running with Android 6.0 or above. And it will quickly support more new Android devices once they are released. But it doesn't work on Android devices with an unresponsive touch screen.
-
What happens when you factory reset your phone?When you factory reset your Android, the disk inside your Android is formatted. It only means that all the indexes to files, like photos, videos, docs, messages, etc., are canceled, and these original files are ready to be overwritten. This does not mean that all the data on the disk are 100% beyond recovery. It only means that all the indexes to files like photos, videos, docs, messages, etc., are canceled, and these original files are ready to be overwritten. These data are always recoverable with industrial data recovery tools before they are entirely overwritten.
Android Data Eraser
Android Data Eraser ensures that your privacy is safe by permanently erasing deleted files, clearing browsing history, caches and protecting your personal information.

Keep Your Mobile at 100% with Our Complete Mobile Solution

Recover deleted or lost data from 6000+ Android phones and tablets.
All-in-one data management solution. Back up and manage phone data, and mirror your phone screen to PC.

Remove various lock screens from your Android devices without a password.