A keylogger can be either a piece of programming or an equipment gadget that can catch the keystrokes composed on the PC's console. A product keylogger can be run behind the scenes and not get seen by normal clients. They'll need to rely upon security programming like an enemy of keyloggers or antivirus bundles to disclose to them a malwarebytes keylogger, more than likely they will have no clue about those things they do on PC are being checked.
Part 1: What Is Keylogger?

Keylogging is a method that programmers use to duplicate (or log) the keystrokes of the client and in this way, extricating financial balance subtleties and other touchy information. The alleged Kernel keyloggers are exceptionally difficult to distinguish, as they "stowaway" themselves somewhere inside the working framework. A portion of the further developed wrongdoing product can even discover its way into your antivirus' rundown of avoidances (the whitelist).
Part 2: How Keylogger Works and How Hackers Use Keylogger?
How a keylogger function relies upon the sort of keylogger it is. Equipment and programming keyloggers will work diversely because of their medium.
Most workstation consoles plug into the rear of the PC, keeping the associations out of the client's view. An equipment keylogger may likewise come as a module that is introduced inside the actual console. At the point when the client types on the console, the keylogger gathers every keystroke and saves it as text in its own smaller than expected hard drive, which may have a memory limit of up to a few gigabytes. The individual who introduced the keylogger should later return and eliminate the gadget to get to the data that has been accumulated. There are additionally remote keylogger sniffers that can catch and unscramble information bundles moved between a remote console and its recipient.
A typical anti-keylogger software ordinarily comprises of two documents that get introduced in a similar index: a unique connection library (DLL) document that does all the chronicle and an executable record that introduces the DLL document and triggers it to work. The keylogger program records every keystroke the client types and occasionally transfers the data over the web to whoever introduced the program. There are numerous alternative ways that keylogging programming can be intended to screen keystrokes, including snaring console application program interfaces (APIs) to another application, noxious content infusion, or memory infusion.
There are two primary kinds of programming keyloggers: client mode keyloggers and piece mode keyloggers. A client mode keylogger will utilize a Windows API to capture console and mouse developments. GetAsyncKeyState or GetKeyState API capacities may likewise be caught relying upon the keylogger; nonetheless, these scan for keyloggers the assailant to screen each keypress effectively.
A portion mode keylogger is an all the more impressive and complex programming keylogging strategy. It works with higher advantages and can be more earnestly to situate in a framework. Bit mode keyloggers will utilize channel drivers that can capture keystrokes. They can likewise adjust the inward Windows framework through the portion.
Some keylogging projects may likewise incorporate usefulness for recording client information other than keystrokes, for example, catching whatever has been replicated to the clipboard and taking screen captures of the client's screen or a solitary application.
Part 3: How to Detect, Prevent and Remove Keylogger?

Keen anticipation rehearses are the most ideal approach to keep away from this deep-rooted danger. However, before we get to those, here's the way to ensure you're getting keylogger removal.
Install a legitimate antivirus: Keyloggers can live in a few spots inside a gadget, making them particularly hard to identify physically. Be that as it may, antivirus arrangements can clear a whole machine rapidly and effectively, saving you time and bother. Be careful with free arrangements, however, because, in-network protection as throughout everyday life, you get what you pay for.
Mark-based antivirus arrangements- those that quest for dangers dependent on a static rundown of known dangers—ought to likewise be kept away from since they're handily tricked. On the off chance that a keylogger is distinguished, an antivirus will likewise be the smartest option for eliminating it.
Update all your applications: Patches and security refreshes are delivered which is as it should be. Weaknesses that could open a client to the establishment of a keylogger are regularly settled. Clients can likewise utilize this as an ideal opportunity to cleanse their gadgets of rarely utilized applications that could unnecessarily represent extra danger.
Manage consents: Continuously be careful with applications mentioning consents that appear to be unreasonable. For internet browsers, occasionally clear your store, erase treats, and eliminate any program modules you don't commonly utilize. Once more, this is acceptable practice for generally speaking digital cleanliness, so it's a beneficial routine paying little mind to the danger you're worried about.
The above advances are useful for the discovery and expulsion of keyloggers. However, to forestall contaminations in any case, as well as utilizing an antivirus, understanding social designing assaults is the best protection. While it may not seem like a silver slug, this implies that fundamental prescribed procedures for network safety are additionally the ones well on the way to shield you from this danger.
Utilize two-factor validation where conceivable and think before you click. Keep in mind, keyloggers can be conveyed through similar techniques utilized by phishing assaults, which implies clients should be continually watchful against unusual or sudden correspondences from obscure senders.
Part 4: Is Keylogger Spyware and Other Types of Spyware?

Keyloggers spyware is a type of spyware that catches each keystroke you type; they can send this data to distant workers, where sign-in data - including your passwords- - can be extricated and utilized.
Keyloggers are utilized to take individual data, login accreditations, and delicate information by following the keystrokes of your console. They're utilized by cybercriminals, yet additionally businesses' to notice PC movement and guardians to oversee their youngsters as they utilize the web.
Other Types of Spyware
Adware: Adware alludes to undesirable programming that conveys publicizing messages to you, through flag advertisements, popup promotions, or redirection of your web perusing. Adware is a sort of spyware that consequently downloads to follow your perusing information with the expectation of foreseeing the items and administrations you're keen on. It will at that point show notices for those items or administrations to persuade you to click and purchase.
Password Stealers: As their name would propose, these kinds of spyware will gather any passwords embedded into a tainted gadget. These may incorporate things like framework login accreditations or other such basic passwords.
Password Stealers are the same as info stealers, the lone contrast being that they are exceptionally intended to take login accreditations from contaminated gadgets. First identified in 2012, these bits of spyware don't take your passwords as you type them. All things considered, they connect themselves to the program to extricate all your saved usernames and passwords. Likewise, they can record your framework login certifications.
Most secret word stealers are regularly eliminated by dependable security programming, however, a few sorts figure out how to keep away from location by changing their record hashes before each assault. Similarly, as with info stealers, the makers of secret key stealers can pick whether they need to store the gathered information on a distant worker or in a secret record on your hard drive.
Modem Hijackers: With the slow shift from dial-up to broadband somewhat recently, modem ruffians have become a relic of days gone by. They are maybe the most established kind of spyware that would assault its casualties while they were perusing the web. When in doubt, a spring-up promotion would show up, inciting the client to tap on it. At the point when they did, it would start a quiet download of a record that would then assume responsibility for their dial-up modem.
Once responsible for the PC, the modem ruffian would separate the telephone line from its present nearby association and rather interface it to a global one. Most programmers would collect premium-estimated telephone numbers (generally proposed for grown-up talk lines) that were enlisted in nations with lacking cybercrime enactment like China, Russia, and some South American nations. The casualties would normally possibly get mindful of the issue when they saw their $1,000+ telephone bill ahead of schedule one month from now.
Browser Hijacker: Browser Hijacker, or thieves, are a sort of malware made to change Internet program settings without the client's information or assent. Ordinarily, criminals change the landing page and default search settings. Nonetheless, some are known to infuse promotions—in this manner, they can be called adware, consequently diverting clients to conceivably noxious objections when they visit certain destinations, and in some cases rolling out intense improvements to the influenced framework. A few robbers additionally contain keyloggers, which are fit for recording client keystrokes to accumulate possibly important data they go into sites, for example, account accreditations.
Part 5: Best 6 Free anti-keylogger Apps for Windows 10.
1. IMonitor

IMonitor Power Keylogger programming is for the most part intended for home clients, it is certainly every one of the one keylogger programmings. Contrasting and other reproduce programming in the market, Power Keylogger is the best across the board utility that incorporates all capacity home clients required, for example, screen catch, contacted key logged, email content inspected, URL history recorded and moment courier talk checked. Incredible and simple to utilize Power Keylogger programming empowers you to see precisely what your mate, kids' and others are doing on your PC in totally secrecy mode.
Feature:
- Always Hidden – Absolutely covertness running, keep away from the application being seen by PC clients.
- Encrypted Log Files – Safely scrambles all log documents that incorporate all outside client exercises, which can be a later ship of the indicated client.
- Password Protection – Password shielded utility keeps others from the beginning or halting the account interaction, just as confine to get to or alter programming establishment settings.
- Keyboard Logging – Secretly record all keystrokes composed on PC which is imperceptible by the current PC client.
- E-mail Tracking - Log all mail messages sent by outside clients in your nonattendance.
- Chat Messengers – Monitors and record visit discussions which make it a predominant observation instrument.
2. Spyshelter
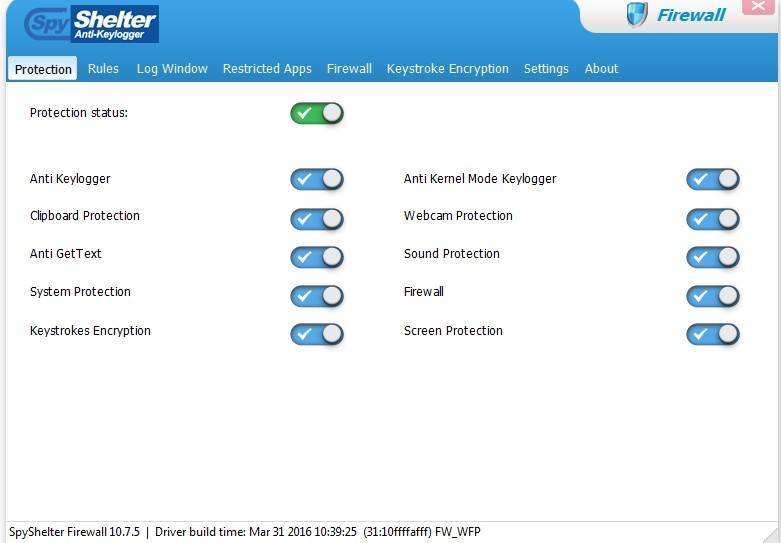
SpyShelter is a free Anti-Keylogger tool, it doesn't depend on an antivirus signature data set, on the grounds that our product sees how malware functions. SpyShelter shields you from both known and unknown dangers, which were not found by antivirus labs yet. SpyShelter Free offers complex framework insurance and against keylogging modules free of charge, just for 32-digit framework clients. It doesn't need account enrollment!
Feature:
- Real-Time System Protection – SpyShelter monitors your library, actual memory (RAM), and other touchy PC parts among with measures, so vindictive code can't be infused to assume responsibility for your PC.
- Anti-keylogger lumberjack – SpyShelter Free Anti-Keylogger guarantees that whatever you type into your PC, is secured against hazardous individuals who need to take your information! With SpyShelter, your information will be protected.
- Clipboard Protection – SpyShelter safeguards touchy information that can be found in your Windows clipboard because of duplicating, cutting, and gluing. Spyshelter guarantees that this data won't be vindictively checked by others.
- Keystroke Encryption – SpyShelter Free Anti-Keylogger has an incorporated keystroke encryption driver which encodes your keystrokes while you are perusing the web. This implies that regardless of whether you permit any noxious application to run on your framework, it will just recover unimportant irregular content.
3. Zemana AntiLogger
This program can perceive, forestall and block a wide range of online fraud and monetary trickery instruments. Monetary malware can profoundly hurt you by acquiring your accreditations which incorporates passwords, usernames, or Visa subtleties. You can get up one morning and discover that your ledger is unfilled. Likewise, your installments can be approved in your name, and we realize that this would be a frightful bad dream.
Feature:
- Zemana AntiLogger is an amazing asset that is additionally simple to utilize.
- It will monitor who is working on your PC, and it screens your framework against programmers, forestalling all efforts to record and taking your private information.
- Zemana ensures that your valuable information gets communicated safely without arriving at any assailants.
- You can likewise disguise your everyday online exercises like calling, messaging, shopping and that's only the tip of the iceberg.
- Zemana AntiLogger accompanies a lightweight and proficient online malware scanner that can distinguish malware and different noxious cycles.
- It is additionally ready to identify and clean your program's additional items and adware diseases.
- Use Zemana, you will find the opportunity to appreciate the best ransomware assurance.
4. KL-Detector
Use KL-Detector to see if your action is being recorded without your insight.
This instrument is intended to recognize every key-lumberjack and that's only the tip of the iceberg. Perhaps the best thing about KL-Detector is that it's free. Investigate additional energizing highlights that are pressed in this program beneath.
Feature:
- KL-Detector is viable with frameworks running Windows.
- The program can't eliminate the keylogger consequently, yet it's simple enough to do this physically.
- KL-Detector reports the log record, and if there is such a long document, there is additionally a keylogger.
- You can utilize this instrument to identify keyloggers in a public PC before you enter your secret word and other fundamental information.
- The programming screens circle composes and reports the composed documents.
- KL-Detector is liberated from adware, spyware, and other undesirable projects.
- You won't have to download the program.
5. Ghostpress
Ghostpress is a cutting-edge free enemy of the keylogging program. It can recognize key-lumberjacks and keep them from catching your keystrokes. This apparatus can manage its work impeccably, and it depends on covering up and controlling the entirety of your keystrokes on an extremely low level. Along these lines, key lumberjacks will not at any point have the option to catch them.
Feature:
- Ghostpress is a direct program to utilize, and you will not need to battle with modern setups.
- This apparatus is adaptable, and you can set the ideal highlights as per your inclinations.
- You will browse bunches of dialects that are accessible in the program.
- The Prevent Hook Overwriting highlight is another fundamental insurance step.
- The programming screens circle composes and reports the composed documents.
- The Whitelist include permits you to pick the applications that shouldn't be observed and which ought to be allowed keylogging.
- It comes in 7 dialects (English, German, French, Italian, Spanish, Korean, and Polish).
6. Keylogger Blocker
Keylogger blocker is a professional for prevent data breaches, it is often referred to as anti keylogger. It consists of a signature based-detection and behavioral monitoring, with it, you can keep programmers from taking your own data. Keylogger blocker can utilize Signature-Based Detection to gather the recorded signature and investigates it. On the off chance that the mark coordinates with any of the infection marks in the information base, the keylogger blocker banners it as a danger and eliminates it from the PC. That is one procedure to recognize and hinder a keylogger.
Feature:
- Keylogger blocker may utilize behavioral monitoring to decide whether the document is malignant by observing its standard of conduct.
- It identifies and hinders various sorts of keyloggers that arrive at your PC.
- It screens the whole organization and endpoint gadgets against keylogger assault by utilizing a solitary control center.
- It forestalls malware from gaining admittance to the part of the working framework.
- It identifies any noxious exercises on endpoint gadgets by observing information transmission on endpoint gadgets.
Conclusion
This article is about the best anti-keylogger for windows 10. We picked probably the best and well-known offers that have been around for quite a while and have wonderful notorieties. As referenced before all else, while free items can likewise be successful, it's enthusiastically prescribed to go with a paid anti-keylogger, particularly in case you're signing into your records consistently.



















Ella Baché
Editor