Malware has become an enormous danger to associations across the globe. Something as basic as possible winds up costing an organization a large number of dollars if the proper controls are not set up. Fortunately, there are plenty of malware analysis tools to help control these digital dangers. Various apparatuses can help security investigators figure out malware tests.
Fortunately, all the malware investigation apparatuses use are free and open source. In this article, we cover my best 6 most loved malware analysis instruments.
Part 1: What Is Malware Analysis and Why We Need It?
What Is Malware Analysis?
Malware analysis is the way toward deciding the reason and usefulness of a piece of malware. This cycle will uncover what kind of destructive program has contaminated your organization, the harm it's fit for causing, and—above all—how to eliminate it. Malware analysis used to be performed physically by specialists in a tedious and awkward cycle. Today, various open-source malware investigation devices can play out this interaction consequently.

Why We Need Malware Analysis?
In case you're a watchful Windows client, you here and there may see a record with a weird or dubious name that you'd prefer to explore. Or then again, in case you're a moral programmer or are in the episode reaction group of an association, you might be entrusted with investigating records to decide if they're authentic or pernicious. In any case, you need an approach to have the option to separate great code and programming from pernicious assortments.
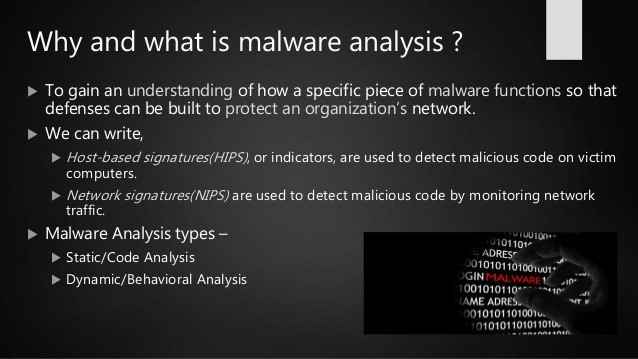
- Decrease hazard of disease.
- Control what gets in and out of your organization.
- Increase your investigation speed.
- Help you assemble a system.
- Help you to distinguish TTP and IOC.
- Have some fun (CTFs, CrackMe, Testing, Exploiting and the sky is the limit from there).
Part 2: Types and Stages of Malware Analysis.
Types of Malware Analysis.
- Static makware analysis.
- Dynamic malware analysis.
What is static malware analysis?
Static investigation analyzes a malware record without really running the program. This is the most secure approach to investigate malware, as executing the code could taint your framework. In its most essential structure, static investigation gathers data from malware without survey the code. Metadata, for example, record name, type, and size can yield hints about the idea of the malware.
Progressed static investigation-otherwise called code examination-takes apart the twofold document to concentrate every part, still without executing it. One strategy is to figure out the code utilizing disassemble.
What is dynamic malware analysis?
Dynamic analysis —likewise called malware conduct investigation—runs the malware program to inspect its conduct. Running a piece of malware consistently conveys some danger, so powerful examination should be acted in a protected climate. A "sandbox" climate is a virtual framework that is secluded from the remainder of the organization and can run malware without hazard to creation frameworks. After the examination is done, the sandbox can be moved back to its unique state without lasting harm.
Likewise, with the static examination, cybercriminals have created strategies to thwart the dynamic investigation. Malware may decline to run if it distinguishes a virtual climate or debugger. The program may postpone the execution of its unsafe payload or require certain client input. To arrive at the best comprehension of a specific malware danger, a mix of static and dynamic analysis is best.
Stages of Malware Analysis.
There are four phases to malware investigation, frequently outlined utilizing a pyramid graph that expands in intricacy as you go further into the cycle. For ease, we'll separate every one of the four phases of malware investigation starting from the earliest stage.
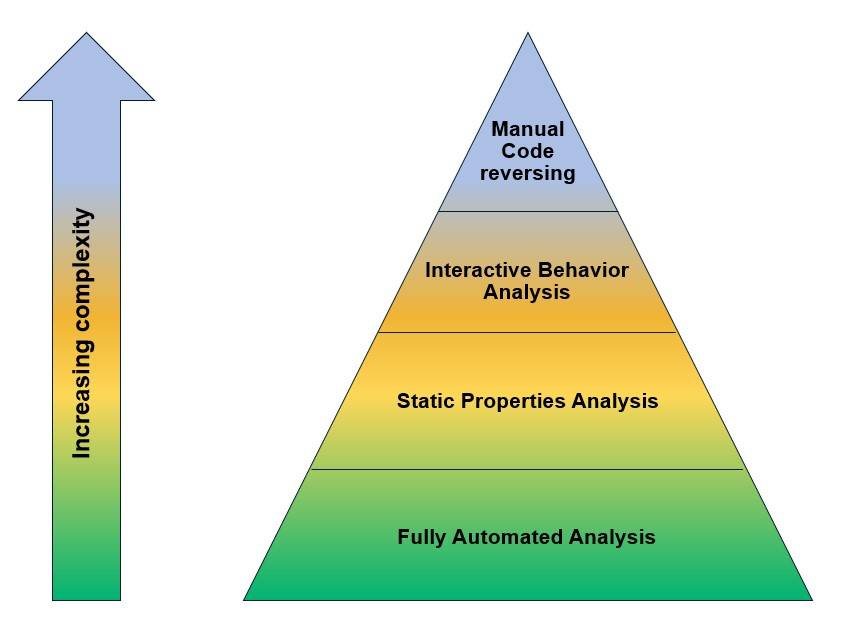
Stage 1: Fully automated analysis:
Mechanized malware analysis alludes to depending on location models shaped by breaking down recently found malware tests in nature. This is the most strategy to measure malware at scale and rapidly survey the repercussions of an example on the organization framework.
Stage 2: Static properties analysis:
Mechanized malware analysis alludes to depending on location models shaped by breaking down recently found malware tests in nature. This is the most strategy to measure malware at scale and rapidly survey the repercussions of an example on the organization framework.
Stage 3: Interactive behavior analysis:
Mechanized malware analysis alludes to depending on location models shaped by breaking down recently found malware tests in nature. This is the most strategy to measure malware at scale and rapidly survey the repercussions of an example on the organization framework.
Stage 4: Manual code reversing:
Figuring out the code of an example malware can give important experiences. This interaction can
- Shed some light on the rationale and calculations the malware employments,
- Expose covered up capacities and abuse strategies the malware utilizes, and
- Provide bits of knowledge about the correspondence convention between the customer and the worker on the order and control side.
Part 3: Best Six Malware Analysis Tools Can Help You.
1. Cuckoo Sandbox:
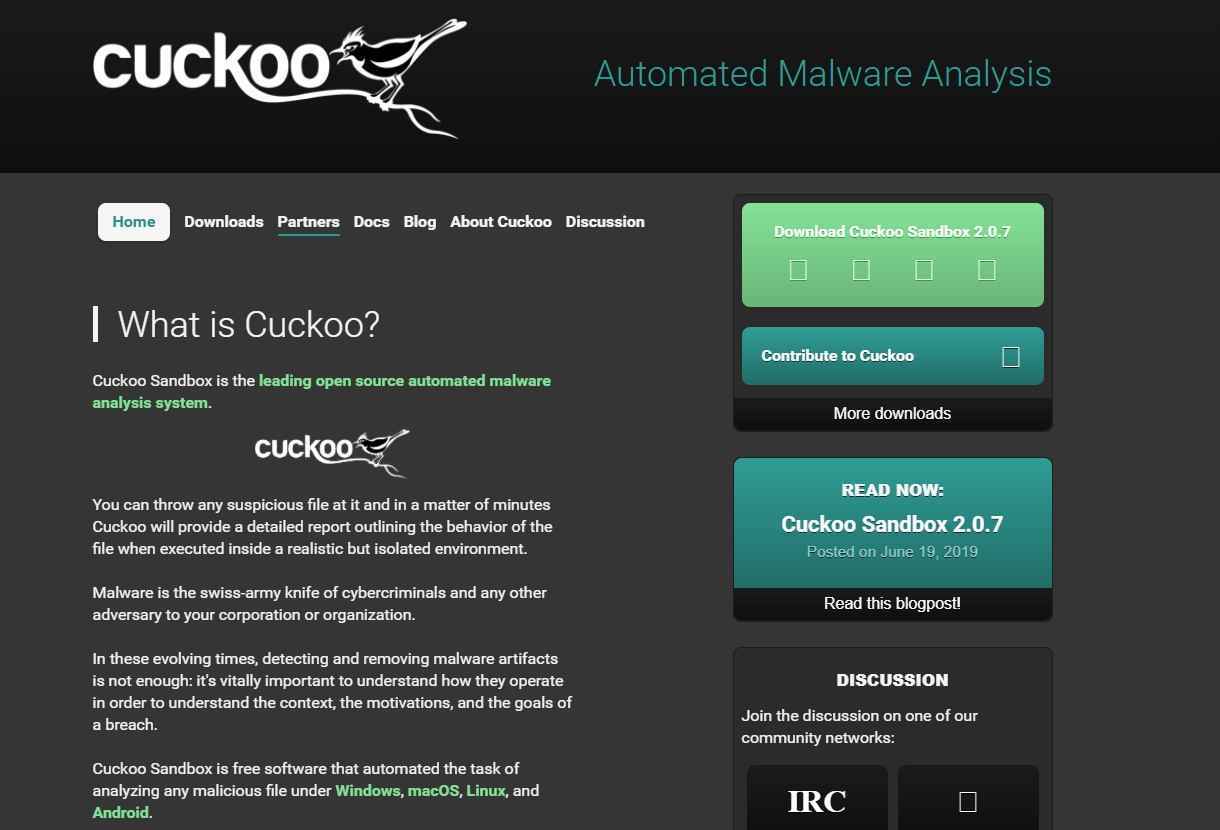
Features:
The conflict between web security specialists and hoodlums is continually raising. For each new safety effort formulated, twelve inventive new dangers crop up. That implies that security experts need to consistently know for new dangers and how to break down them. Cuckoo Sandbox is a piece of legal sciences and investigation programming that assists you with investigating dubious programming, delve profoundly into its segments and decide the danger level and nature of it.
Pros:
A pioneer of malware sandbox structures and still an innovator in the business Open source nature implies that anybody can redesign and adjust it to their impulses Support from over 100 distinct engineers on GitHub.
Cons:
Smaller group and high utilization implies that updates and backing are in some cases moderate Development group can be delayed to react to pull demands.
2. Ghidra:

Features:
- Project Management: Ghidra you start with an answer for which add the executable and its wards which can permit you to hop into the capacity bring in a reliant library.
- Disassembly View: Instruction Info can be utilized as a processor guidance reference – data about the operands, guidance unraveling, and so on.
- Structures: The structure development is utilizing counterbalances just as types (for example HWND, HINSTANCE, LPCTSTR, and so forth); Ghidra can parse a C header and add the distinguished kinds… cool!
Pros:
- Structures: Ghidra can parse a C header and add the recognized kinds… cool!
- Symbol Tree: APIs have effectively recognized the boundaries and their sorts are now populated.
- Decompiler Tree: It is feasible to alter the printed decompiler by renaming capacities, change models, change variable names, and so on.
- Function Editor: Available to change the calling show, add custom shows (same as IDA).
- Code Patching: Same as IDA utilizing the Memory View.
Cons:
- Ghidra is all Java.
- It supports investigating.
- It supports fewer record designs (document parsers/loaders).
3. PeStudio:
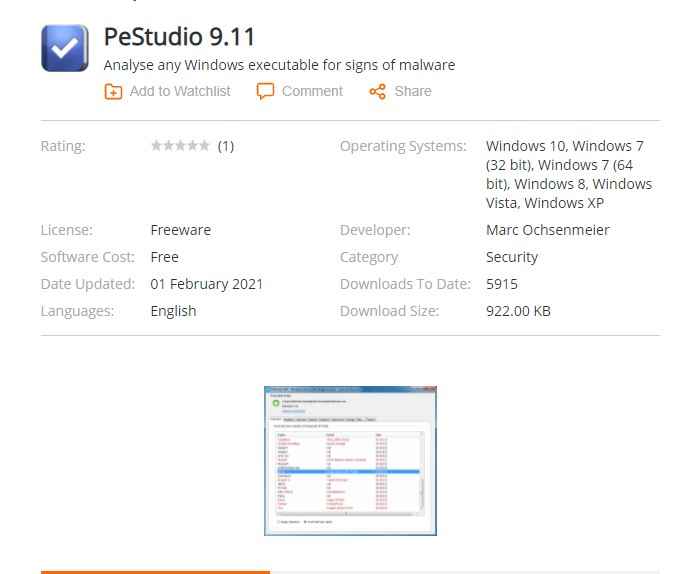
Features:
- All libraries are utilized by an application.
- All capacities that are imported by an application.
- All capacities (additionally mysterious) that are traded by an application.
- All capacities are sent to different libraries.
- Obsolete Functions that are traded and imported by an application.
Pros:
- Do what the producer says.
- show astounding insights concerning applications
- Be installed finely on Windows 7 Home Premium. It gives extremely nitty gritty data.
Cons:
- As the creators say, cart on Windows 7 64 bit.
- Crash when you click 'Imported Libraries' with a record open.
4. Joe Sandbox:
Features:
- Developed by Joe Security.
- Proprietary and Freemium item..
- Subscription.
Pros:
- Usability, granularity, and exactness of results, cookbooks. Incredible revealing.
5. Wireshark:
Features:
- Deep assessment of many conventions, with really being added constantly .
- Live catch and disconnected investigation.
- Standard three-sheet parcel program.
- Multi-stage: Runs on Windows, Linux, macOS, Solaris, FreeBSD, NetBSD, and numerous others.
- Captured network information can be perused through a GUI, or through the TTY-mode TShark utility.
Pros:
- Free programming.
- Available for various stages - Windows and UNIX.
- Can see nitty gritty data about bundles inside an organization.
- Not restrictive can be utilized on various merchants dissimilar to Cisco Prime.
Cons:
- Notifications won't make it clear if there is an interruption in the organization.
- Can just assemble data from the organization.
- Steep expectation to learn and adapt.
6. Autorun:
Features:
AutoRuns is a convenient and easy-to-utilize application that can help you in such a manner. It offers inside and out investigate autostart sections and allows you to impair applications that you would prefer not to dispatch consequently when you turn on the PC. It's allowed to utilize and allows you to take depictions with settings for correlation purposes.
Pros:
- Use for free.
- Clear UI, making it simple to check every dynamic cycle and project.
- Track all introduced projects and cycles.
Cons:
- Some malware applications probably won't be enlisted inside dynamic cycles, making it here and there futile when identifying issues.
- Deleting or handicapping measures will not eliminate any remainders of pernicious projects from the hard plate drive.
- Infections and issues that show up on numerous client records may be eliminated per client account.
Conclusion
Malware Analysis can be hard, yet it will be enjoyable. It's not just running examples and dismantling code, and you'll open yourself to a variety of advancements, structures, and difficulties over the long run. There is an incredible need for these capacities on the lookout and a lot of sources where you can gain from.



















Ella Baché
Editor